Hardware Design and Power Analysis Attack of AES
Breaking AES encryption through side-channel vulnerability analysis using Correlation Power Analysis (CPA) attacks
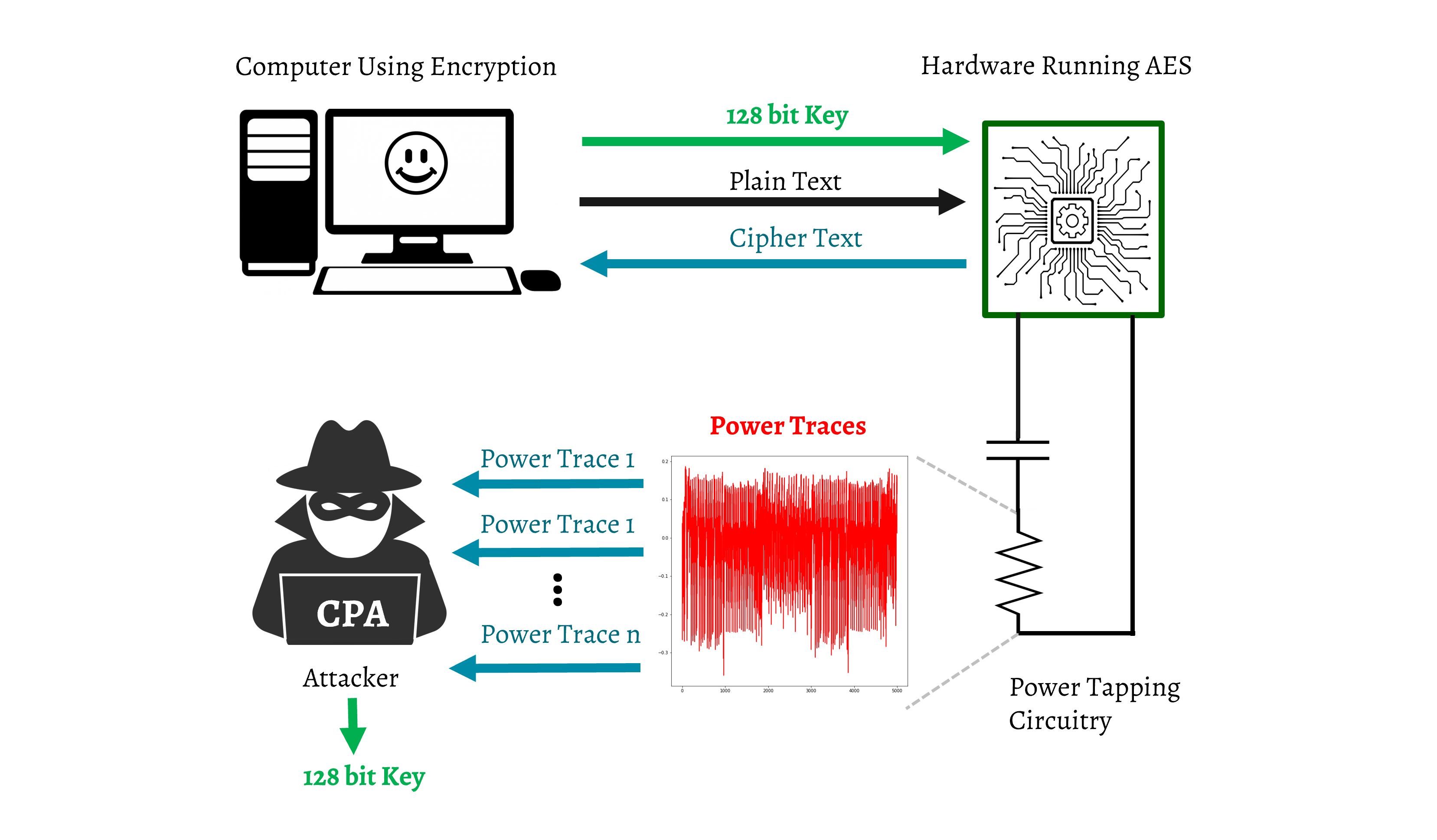
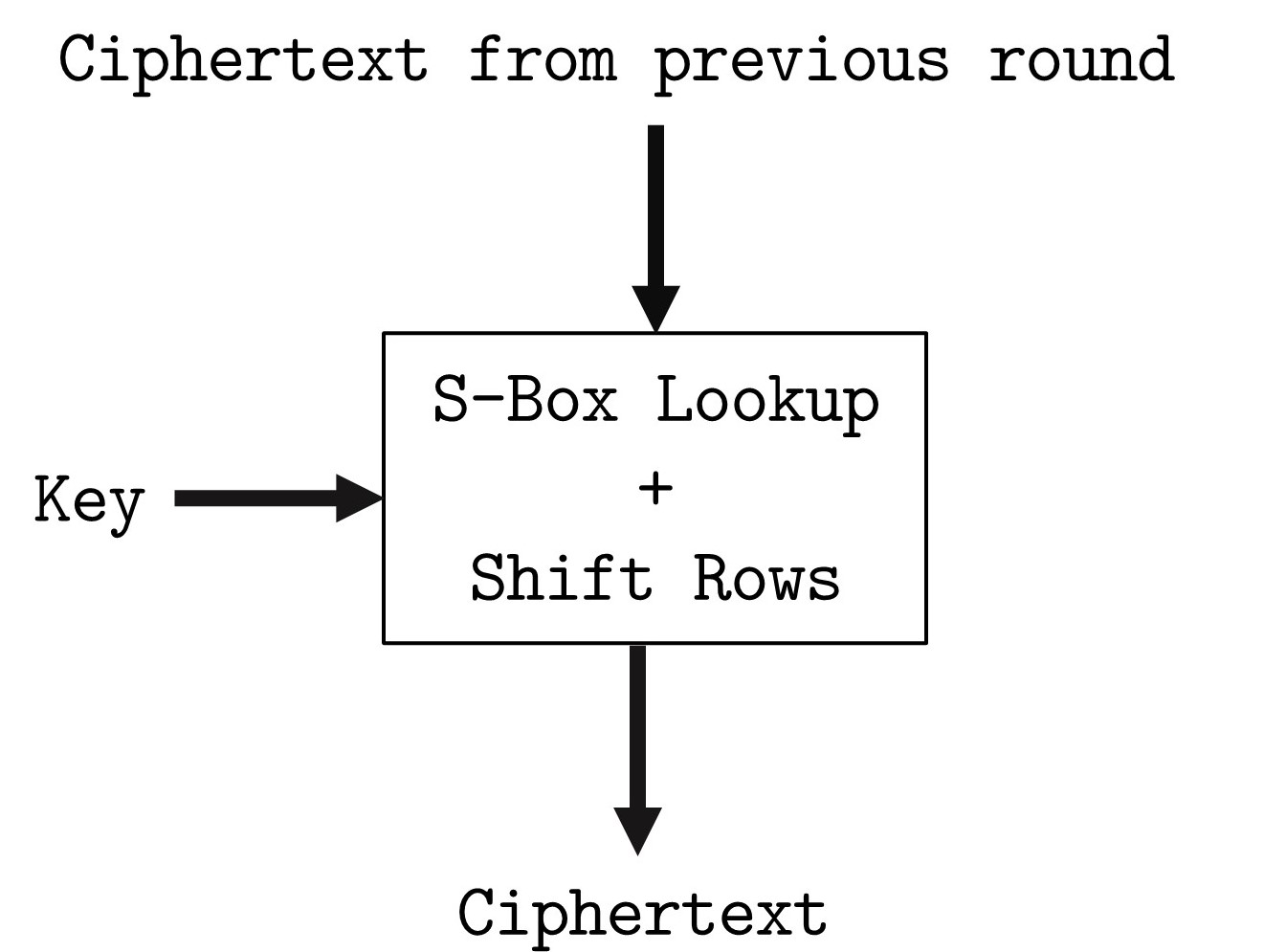
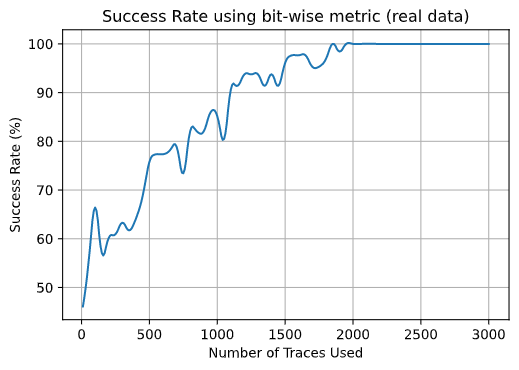
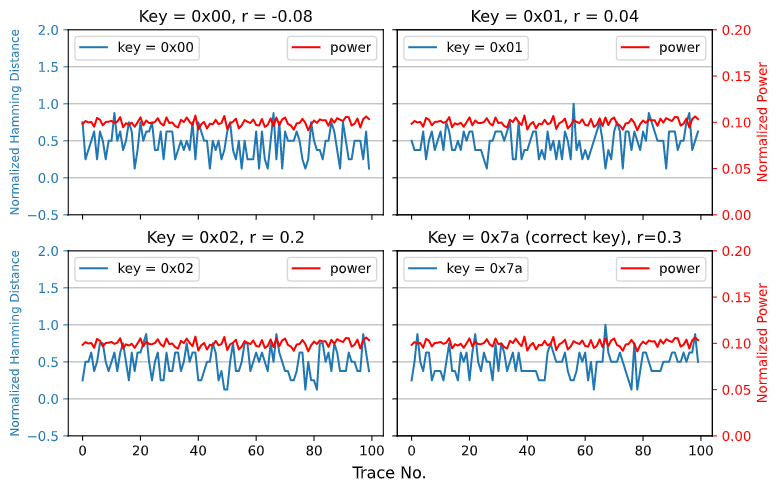
This project seeks to break the most widely used symmetric cipher, the Advanced Encryption Standard (AES) by exploiting it’s side-channel vulnerability when operational in hardware, thus enabling an attacker to implement side-channel analysis techniques like the Correlation Power Analysis (CPA) attack to retrieve the encryption key. A successful CPA attack can replace an exhaustive key search, which would need 2^128 computations in the worst case scenario. An iterative key search in CPA would run 256 times for each key byte, ultimately reducing the computationally secure problem to a trivial one.

Technologies Used: Python, C++, LaTeX
Project Link: GitHub Repository